
Vehicle theft is becoming a growing problem. Thieves are very organized and can steal a vehicle in seconds as statistics show all over the world. Meanwhile, police fail to recover more than half of stolen vehicles. For criminals, it is a low-risk way of making a fortune,
According to Interpol, the use of the Internet has contributed to a dramatic increase in the resale of illicit automotive components in recent years.
This has become a worry for car owners, insurance providers, and car manufacturers.
Most anti-theft solutions are run by a vehicle's central command, which is easy to override.
Stolen vehicle recovery has become more convenient with IoT technology and GPS sensors.
IoT devices that can be installed in cars have low maintenance costs and are energy-efficient.
The devices that are small and easy to conceal can be fitted in multiple spots in a car.
They can get a stolen vehicle’s location based on the slightest signal, and they also offer a wide area of coverage.
So in our design, we aimed to show the intelligent use of FPGA and Azure IoT in detecting thefts very easily.
Features:
1) GPS tracking
2) Interactive user interface
3) Owner's Face recognition
4) Towing detection
5) Vehicle engine blocker(Blocks engine starter when jammer detected)
6) Manual & autonomous driving modes
Demo Video
Project Proposal
1. High-level project introduction and performance expectation
Purpose of the design:
According to Interpol data, illicit trafficking of vehicles generates an estimated 19 billion USD of criminal earnings worldwide every year and the number is growing. To prevent these attacks, we aimed to use the FPGA intelligently in such a way that theft cannot steal a vehicle even in the jamming condition and we create a user-friendly interface to see the vehicle's location and can see who is inside the car. To make the theft detection very fast even in seconds we are placing FPGA as a central command to our project. We've chosen Microsoft Azure IoT to make the communication faster between the device & user and alert the owner instantly and share the data of and theft images & vehicle's location with the owner. Vehicle past locations, and theft photos are automatically stored in MICROSOFT AZURE. The owner can easily access the vehicle's history stored in the Microsoft cloud.
Application scope:
The scope of this project is to fulfill the best performance FPGA in detecting thefts within seconds. Since the device warns instantly, the vehicle is still close to the owner's location. So that owner immediately catches the vehicle. With this instant recovery of a stolen vehicle, we can prevent attacks worldwide and decrease the no. of attacks every year.
Detecting theft:
Preliminaries:
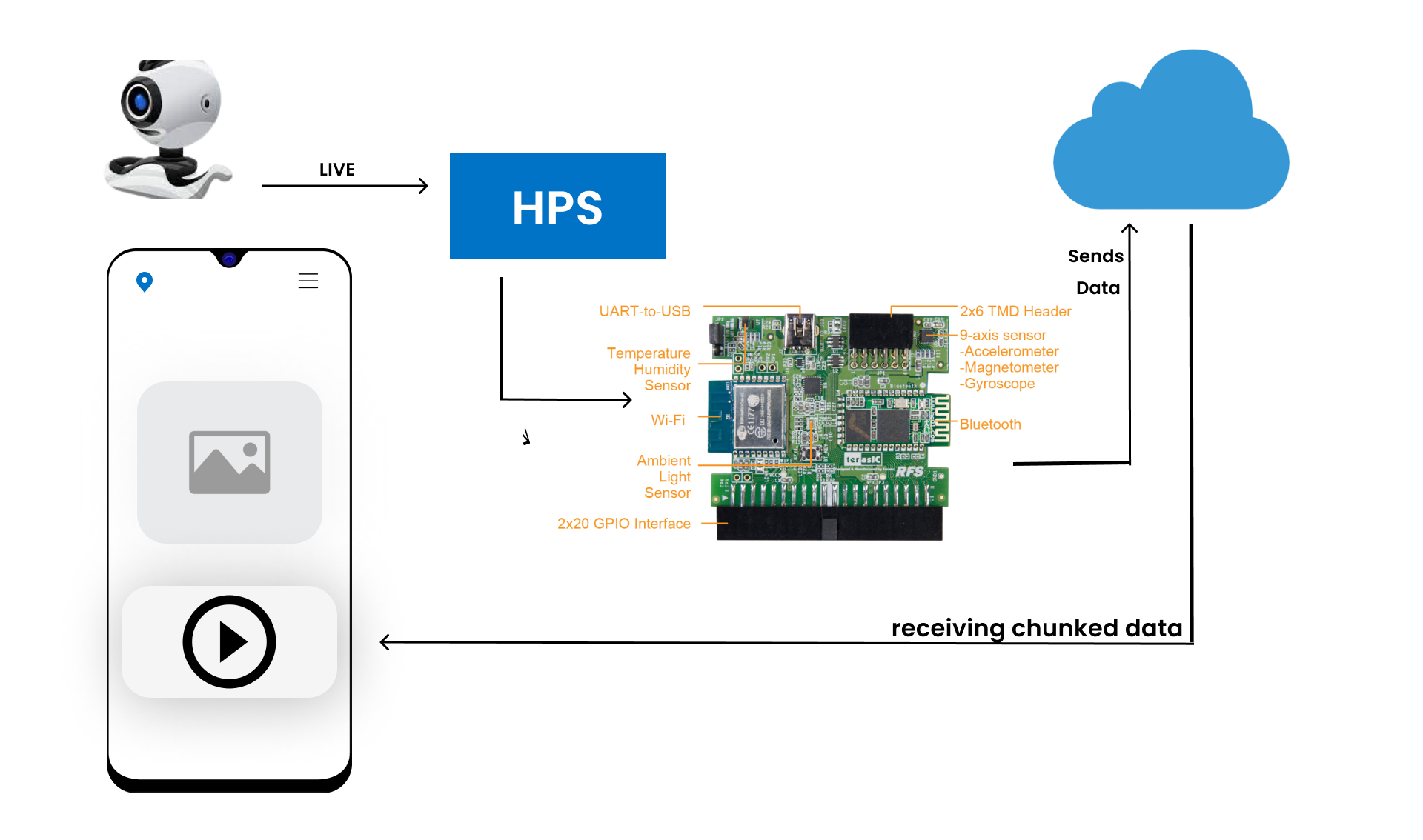
Here, the DE10Nano device is acting as a root for the whole system. Sensibly, if something occurs in DE10Nano inter-connections the system will collapse and will never start until it should resolve. The root device should connect to the internet before turning on the system.
We are using 2-step verification by sending a cipher to the root system while trying to register the owner's phone to the owner's vehicle to gain control access to a vehicle from the phone.
Case- I:
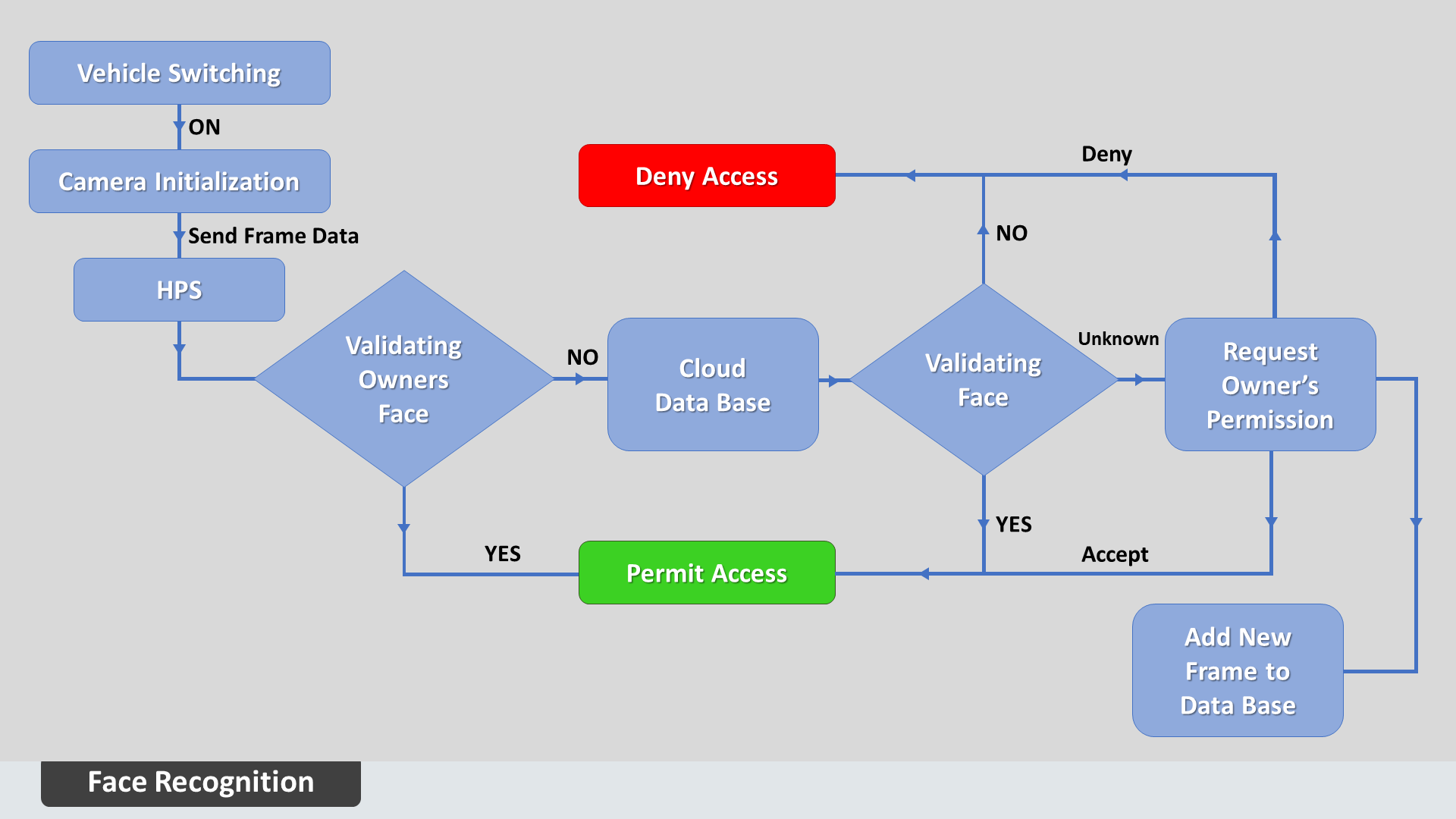
By Recognizing the owner's face. We have designed an Algo to recognize the owner's face even in the nightlight. If the owner recognition fails then the algorithm will check again in a large database for thief's face confirmation in the cloud using Azure services. After a lot of conditions and confirmations, the Algo will send the notification to our Android Application which is installed on the owner's phone. From there, the Owner can permit or deny access to the unknown person.
Case-II:
What if the thief steals the phone of the owner and confirms himself as an owner? What if the thief disconnects the internet after gaining the driver's access? We have developed AI for Autonomous driving to drive back to the previous initial point or GPS location.
Case-III:
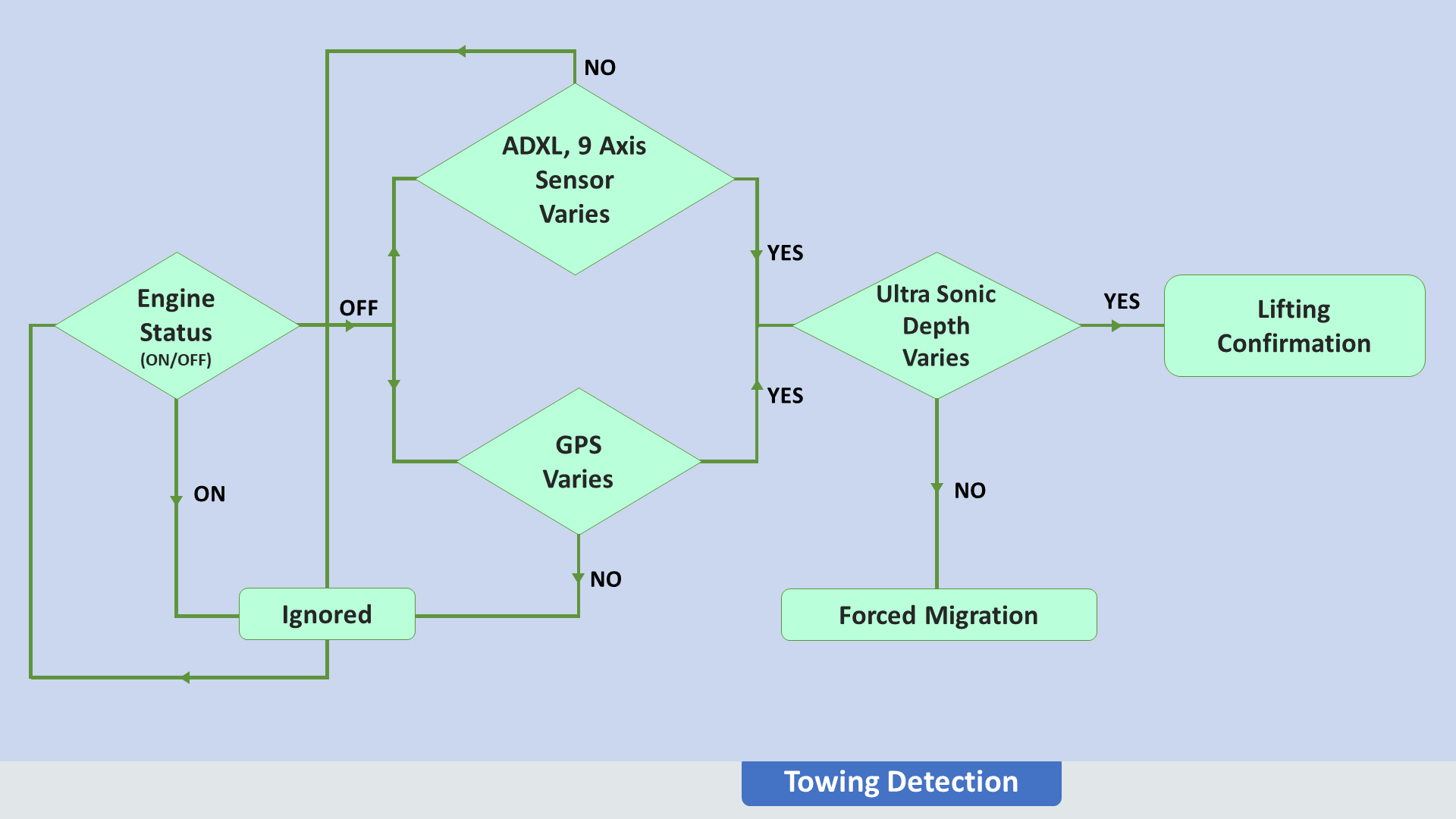
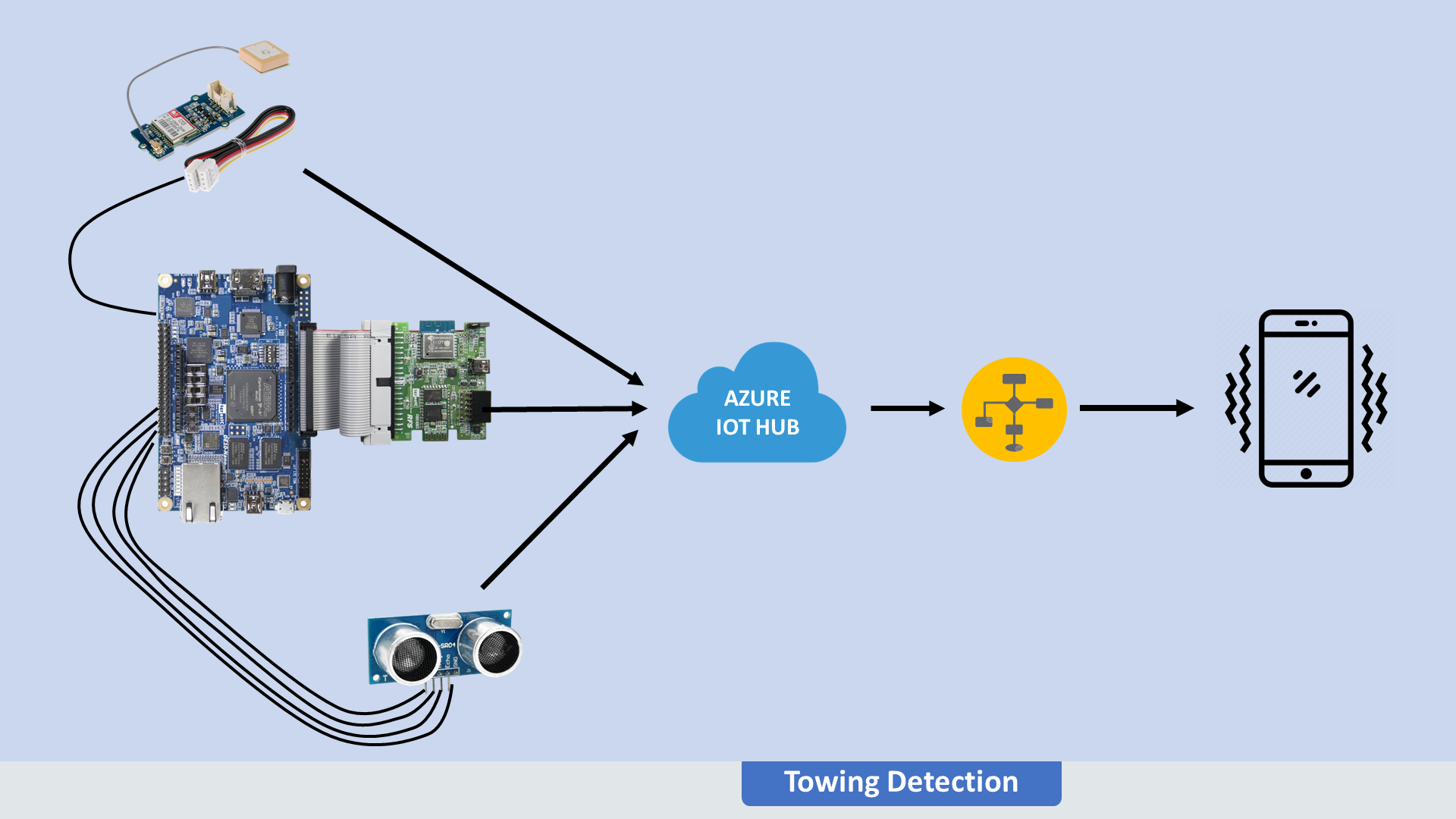
What if someone tries to steal our vehicle by lifting it like using a Crane machine or by pushing our vehicle forcibly into another vehicle? Using the ADXL sensor, 9-axis sensor and by checking the depth under our vehicle, we will confirm and will make the decision to send a notification to the owner's phone will GPS location tracking points.
Case-IV:
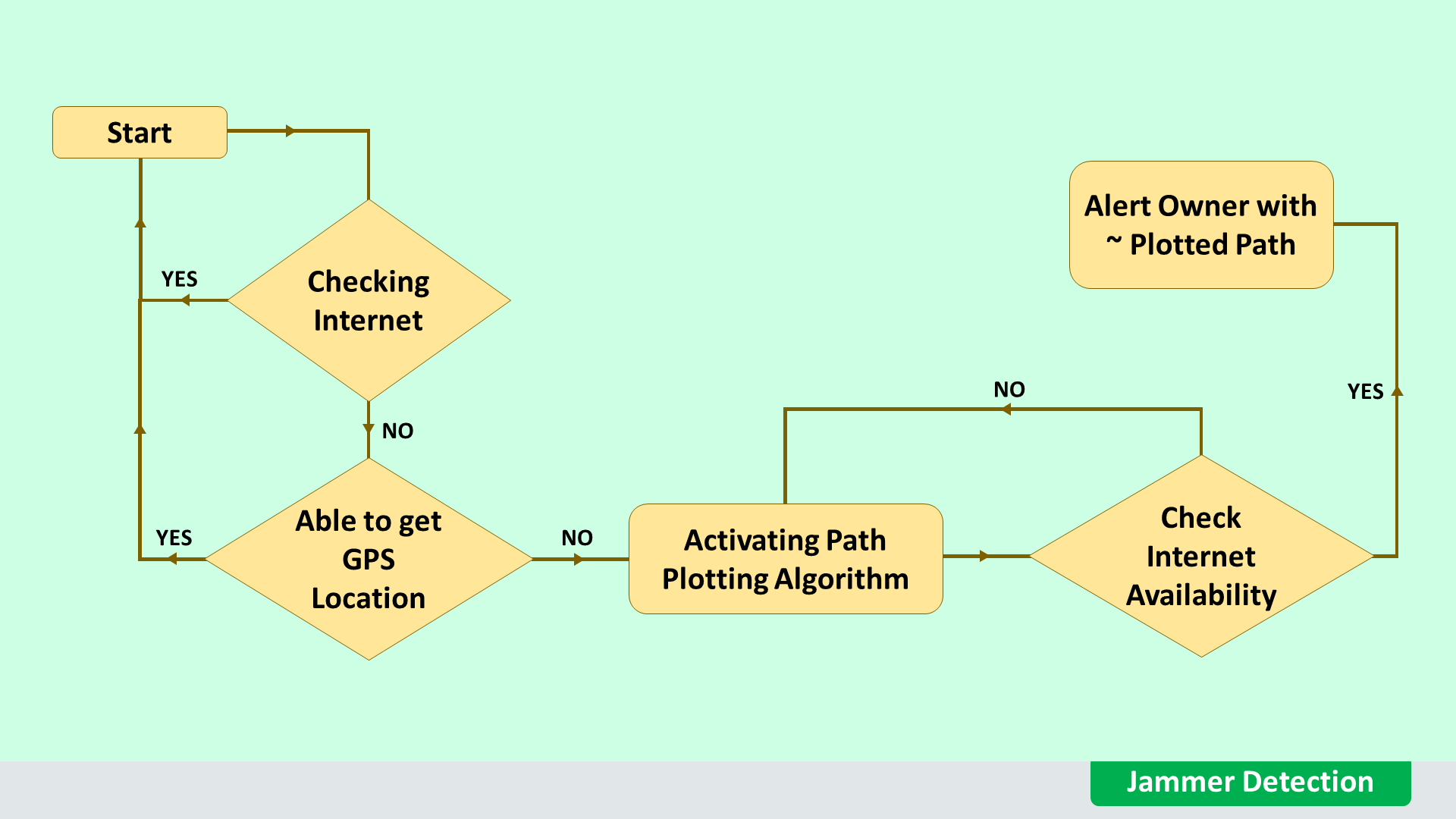
What if the thief tries to collapse the internet connection using a jammer to stop communication between the vehicle and the cloud? To resolve this issue we have developed an Algo to detect whether the particular noise signal is coming from a jammer or not.
https://www.youtube.com/watch?v=CKK9iJFi7cE
Targeted users:
This device is currently a prototype of theft detection that will be very useful in vehicles with an in-built wifi connection. With the help of this device, the owners can make their vehicle more secure and it will also become the best device for vehicle owners, insurance providers & manufacturers.
Why intel FPGA?
The Intel FPGA includes interfaces such as ethernet and SPI which give the flexibility to store the data directly onto an SD-CARD. The FPGA also includes A/D converters and an i2c bus which makes it simple to integrate with sensors such as camera and GPS which are necessary to detect the thief and share the live location. And also lesser power consumption and latency by using embedded FPGAs. Hence we choose FPGA as the central command for all devices in our prototype to make our project more flexible.
Why Microsoft Azure Cloud?
As we described in the prototype, the owner can able to see the past location history and thief images. To store this whole data we have chosen Azure cloud because it is the most secured and trusted platform to store the data. And the Microsoft cloud has the flexibility to access the data at any time & any place. And It is impossible to lose data that is stored in the cloud.
2. Block Diagram
System Block Diagram:
.png)
System flow diagram:
.png)
GpsLocation
.jpg)
CameraView:
3. Expected sustainability results, projected resource savings
As per the past records on criminal cases, many of the stolen vehicles are not recovered yet, and with the help of the police also many people are losing their vehicles. In order to make the vehicles more secure and prevent those attacks from thieves, we have chosen the IoT technology. In this technology, we have placed FPGA as the central command for all the gadgets we have used.
The FPGA parallel operation capability provides better results within seconds, It has the ability to detect the thief as soon as the thief enters the vehicle. Hence with the help of this device, we can easily reduce the crime rates which are gradually increasing every year. As mentioned in the description, IoT devices installed in vehicles have low maintenance costs and are energy efficient. So we can achieve the best sustainable results with less cost and energy. And the devices are very small though we can easily set them up in multiple spots in the vehicle.
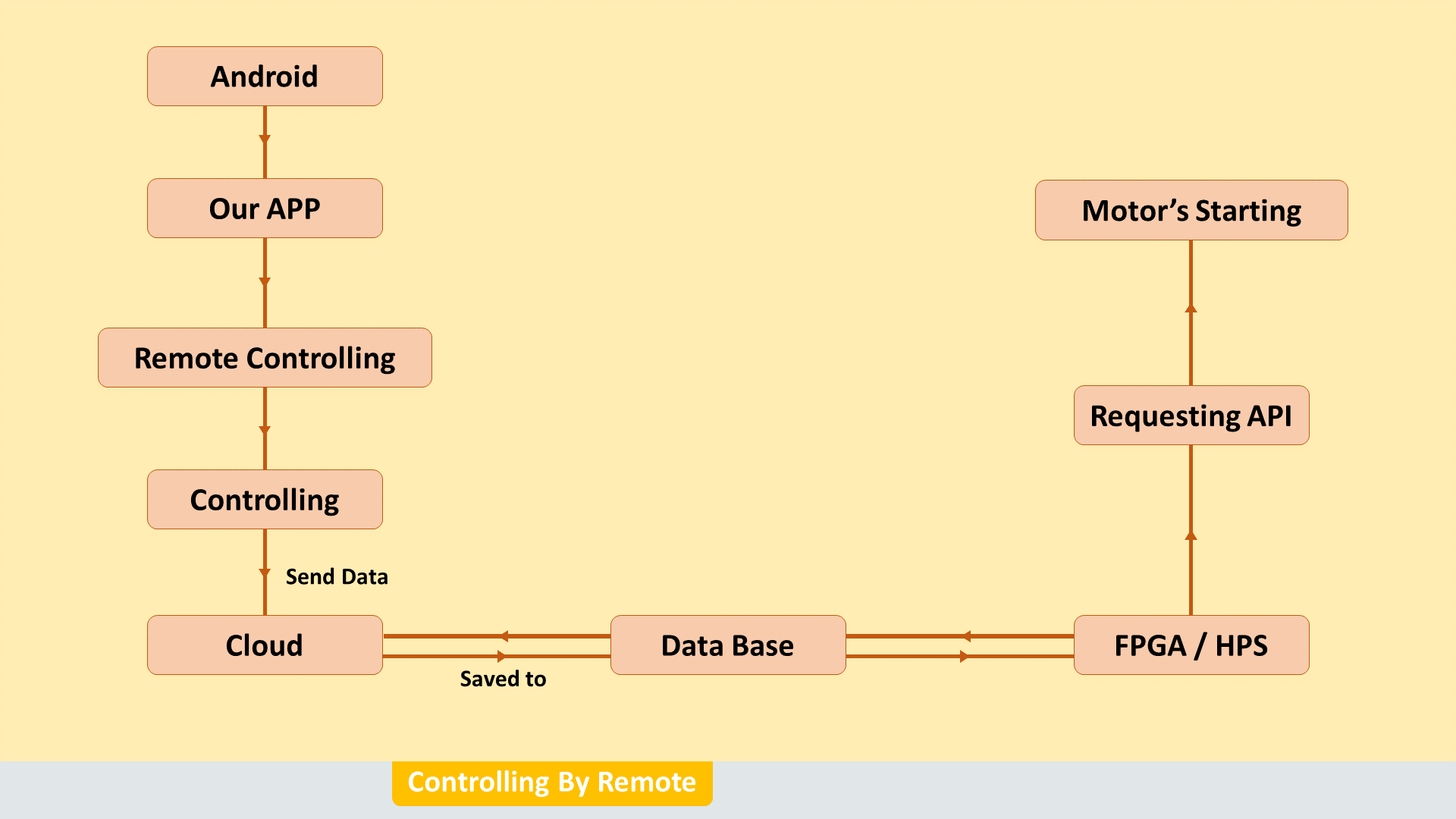
In order to provide a friendly user interface, we will design a mobile program, which can be useful for the owner to see who is actually inside the vehicle and track the location of the vehicle when theft is detected. Through the mobile app, the owner can easily access the past vehicle location history and thief images. Although, we can also control the behavior of the vehicle by controlling motors, car doors, and Engine power supply and can decide the driving mode of our vehicle. Once the driving mode has been changed then the manual control has been disabled.
4. Design Introduction
Our system is designed in such a way that has multiple threads and can detect any way of theft very accurately. But, our design needs to access data from many analogs and digital components/sensors through GPIO from the HPS part of the DE10Nano. While using the LXDE operating system, the GPIO's are not defined internally means GPIO's register addresses are not connected to LXDE. So have we changed the DE10_NANO_SOC_FB.rbf based on Xfce operating system. After then We have changed the "terasic-de10-nano-kit" operating system files which are the only ones supported for Azure Cloud connection. Finally using the AXI bridge, we register the base addresses of GPIO in "terasic-de10-nano-kit". Then, we have overwritten the resulted lib/firmware/overlay.dtbo with our modified overlay.dtbo . Finally, got access to GPIO in CloudPre-Installer {LXDE}. Now, we have used GPIO for vehicle key switching, ultrasonic sensors, GPS sensors, etc... GPS sensor is for tracking and locating our vehicle's GPS point. The ultrasonic sensor is used for finding out the depth under the vehicle if a thief proceeds towing method to steal our vehicle. And we have used the internet through USB tethering because of to escape from jammers and for fast internet.
From RFS Daughter card, We have used the ADXL sensor, a 9-axis sensor. ADXL is for detecting the movement of a vehicle when the vehicle is in the off state. And, the 9-axis sensor helps us very much when our vehicle is under jamming to plot the path of vehicle movement.
5. Functional description and implementation
My main motto for this design is to stop or reduce vehicle thefts. For that, We have designed a sort of algorithm to stop thieves from stealing others' vehicles. If in any case, my algorithm failed because of bad predictions then also we can recover the stoled vehicle with a Redundantalgorithm that is already developed for these types of scenarios by storing sensors and image processing data. My whole design is implemented on LXDE which is booted on HPS part of the DE10Nano.
This design helps many vehicles owners in such a way that to locate vehicles, can able to track their vehicles, and can also see what happening inside the vehicle from their mobile application when they are not present in the vehicle. This design also reduces criminal cases regarding vehicle stolen cases.
Field Programmable Gate Arrays (FPGAs) are semiconductor devices that are based around a matrix of configurable logic blocks (CLBs) connected via programmable interconnects. FPGAs can be reprogrammed to desired application or functionality requirements after manufacturing. They are very fast compared with other microcontrollers. This project is to fulfill the best performance FPGA in detecting thefts within seconds. Since the gadget cautions in a flash, even the vehicle is still near the owner's area. So the proprietor quickly gets the vehicle status iff anything occurs suspicious. So that we can recover the vehicle instantly and we can also prevent attacks worldwide.
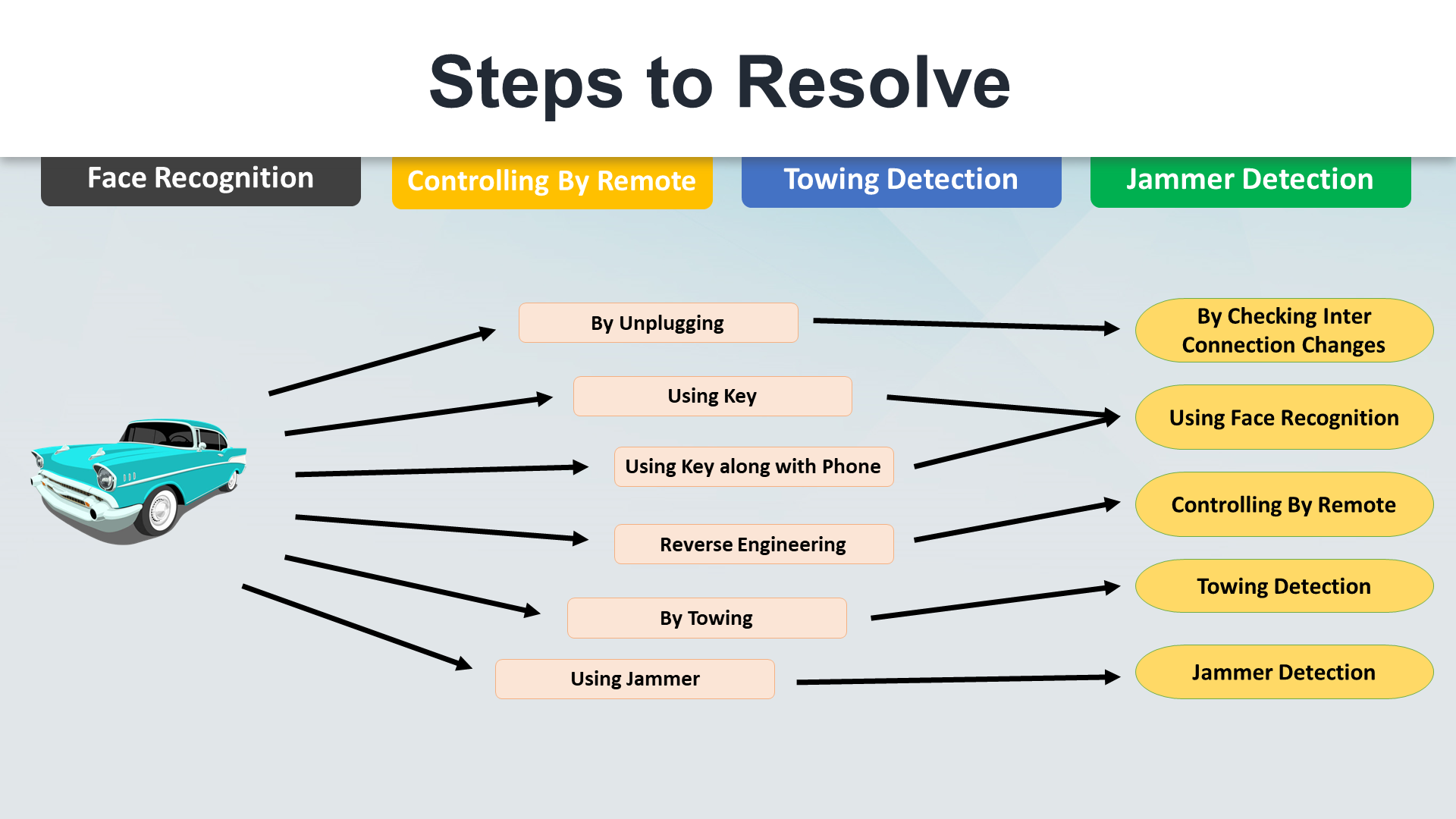
We have had divided our design into multiple parts based on the type of attack. In a general case, the attacker thinks very broadly before he/she give it a try.
After a lot of research, we have found some ways and had designed some algorithms to prevent those attacks. Firstly, we tried to understand the psychology of the thieves. So based on their way of thinking we have had to implement some methods to stop him in his way.
Types of thieves, their ways, and our solutions:
Type-1:
Most of the hoodlums are trying to get access to the vehicle by unplugging the inter-connections at the engine. So that they can get access to the vehicle. But here we also implement some tricky validation on DE10Nano to detect whether the inter-connections are correct or not and if any inter-connection is disturbed then the vehicle will not start until we resolve those connections.
Detailed Implementation:
Actually, unplugging the vehicle means there is no longer a need for a key to start the engine of the vehicle. Unplugging is basically done between the key access connection and engine power supply. So if someone unplugs that connection, then the engine will automatically start if they give external force to rotate the engine. To prevent this, we will strictly check every connection digitally in DE10Nano. So if any of the connections changed internally then we will stop the power supply.
Type-2:
Many of the thieves are trying to steal vehicles by stealing the key of the vehicle from the owner. Nowadays everything is computerized, We also go through the same perspective means drivers need to verify their faces every time even if he/she has the key to that vehicle.
Detailed Implementation:
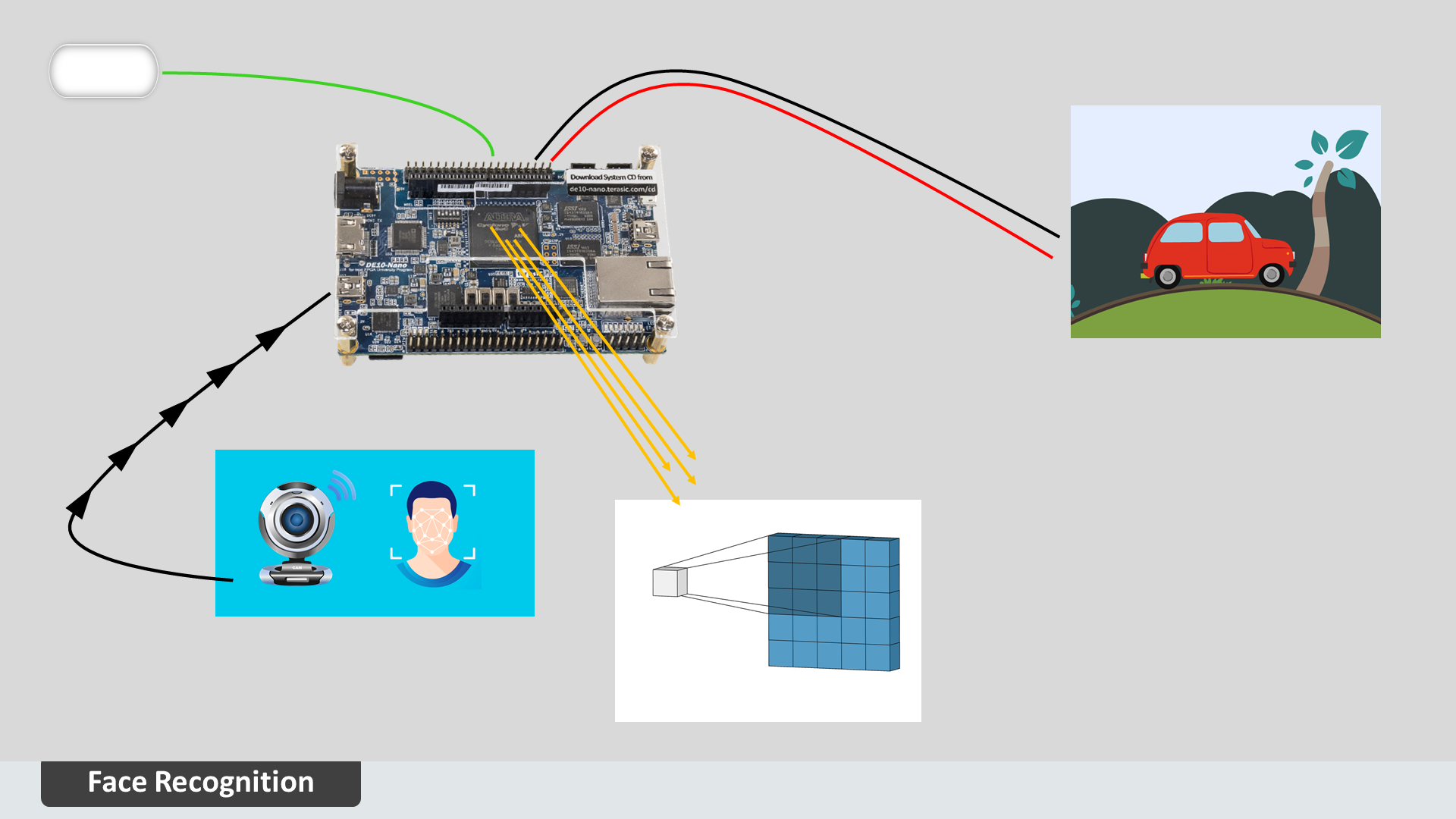
When a thief or an unknown person enters the vehicle and tries to start the vehicle with a key, then my program that has been pre-triggered in the HPS part of the board will instantly initialize the camera module and request image data from the camera. Then the camera will return the image data frames to the requested function. Along with this, another thread is also triggered when the board gets power. That thread will initialize the face recognition program that verifies whether the requested image contains the vehicle's owner's face or not. If the validation confidence is 80% with correct protection, then motors will get power on.
Type-3:
Some of the other thieves are aware of the above prevention, So this time they tried to steal the owner's phone along with the key to accept themselves as the owner of the vehicle. But here we requested a secret hash to accept the new driver.
Type-4:
Literally, some extraordinary thieves do reverse engineering to steal vehicles in a very safe way. They behave very nice to the owner and gain trust. Once the owner gave the driver access to them, then they will try to steal their vehicles. So, in this situation, we will forestall by overriding the vehicle's offline controls and communicate with the vehicle through a mobile application by changing the driving mode or by controlling them remotely.
Type-5:
In a very rare mindset, the thief tries to steal the vehicle by lifting it like using a Crane machine or by pushing our vehicle forcibly into another vehicle. So we are using the ADXL sensor, a 9-axis sensor and by checking the depth under the vehicle, we will confirm and will make the decision to send an alert to the owner's phone will GPS location tracking points [Alert alarm will play in case of this attack].
Type-6:
Suppose the thief is technically an expert and has excellent knowledge in this profession, then he/she will come up with a jammer to collapse the internet connection and GPS to stop communication between the vehicle and the owner B Using the path plotting algorithm we will resolve this issue by storing the speed, ADXL, 9-axis sensors data and will calculate the approximate path with all curves.
In case our vehicle gets internet access then the stored path will be sent to the owner's mobile in a graphical map. And based on the owner's decision the vehicle will come back to the previous location with AI driving mode.
6. Performance metrics, performance to expectation
Our design gives the most accurate results than expected. With low resources, we were able to complete this project successfully. Actually, we expected to step back the vehicle when the vehicle is under jamming, But the resultant results are very satisfactory. With PathPlotting Algorithm we are almost able to achieve our stepBack Algorithm. But, not every car is Autonomous Car so, with our device, we can't make normal cars autonomous cars. But can convert and use them in our way.
The face recognition Algorithm works perfectly and we are able to give 90 correct predictions over 100 cases. Towing detection was also works perfectly. Using RFS details, we figure out the approx path that vehicle travels when under jamming. We are unable to achieve 100% accuracy in path plotting. But I can plot approx path plotting algorithms changed values.
| -----Description---- | -------Expected--------- | ------Reached----- | ------Review------- | -----Reason------ |
|---|---|---|---|---|
| Unplugging detection | Detected every time interconnection changes with 100% accuracy | 100/100 | Excellent | |
| Face Detection | 99% accuracy of detection of owner and thief | 90/100 | Satisfactory | When unknown people wear masks or glasses |
| Controlling by Remote | Able to control the vehicle using mobile easily | 95/100 | Satisfactory | Because of low internet signals |
| Towing Detection | Detect in every case and intimate owner fastly | 99/100 | Excellent | |
| Jamming Detection | Detect Jammer and intimate owner | 100/100 | Excellent | |
| PathPlotting Algorithm | intimate owner with the route when vehicle under jamming and used towing attack | 90/100 | Satisfactory | Sometimes RFS Daughter card gives garbage values |
| Redundant Algorithm | An efficient way to stepBack the vehicle using the Pathplotting Algorithm | 70/100 | Image Processing is very hard to speed up in DE10Nano, and Algorithm used heavy resources. |
7. Sustainability results, resource savings achieved
Our system was designed to prevent vehicles from being stolen. At the same time, we are providing detection algorithms to recover stolen vehicles. After research, we found there are 6 major ways to steal a vehicle. If theft follows any one of the six mentioned cases, our system will give 95% accuracy since we don’t have control over power at this moment. We implemented a face recognition algorithm, path plotting algorithm, jammer detection, and towing detection to prevent and detect the vehicle. Technological advancements in automobile and IoT domains create scope for developing our project to save the vehicle from theft. Our system efficiency will improve with respect to the growth rate in technology. We can survive our vehicles from thefts. So, our property will be in safe hands.
8. Conclusion
Our idea may not result in 100% safety of all vehicles but we are sure that 90% of vehicles can be saved for being theft. We hope our project can be the future for the safety of vehicles.

0 Comments
Please login to post a comment.