NIST announced the finalist who are participating the Lightweight Cryptographic competition for securing small devices which is targeting Internet of Things applications. We are planning to build a reconfigurable processor which runs all of the 10 candidates on FPGA using dynamic reconfiguration. The proposed processor will be evaluated using DE10-Nano Cyclone V SoC FPGA Board
and also Microsoft Azure IoT on both software and hardware perspectives
Demo Video
Project Proposal
1. High-level project introduction and performance expectation
This project aims at the security of tiny devices that are classified as the Internet of things actuators. As NIST luanched a new competition a couple of years ago to define the new standard of both authenticated cipher and hash function which is designed for securing tiny devices. At the moment out of 57 candidates who started this competition, NIST selected ten submissions as a finalist. The project aims an optimized the intensive study of these algorithms on both software and hardware levels to produce a new reconfigurable processor, which can run most or all of them without adding any extra load on the battery lifetime and manage to work under physical constraints the computing devices could have.
2. Block Diagram
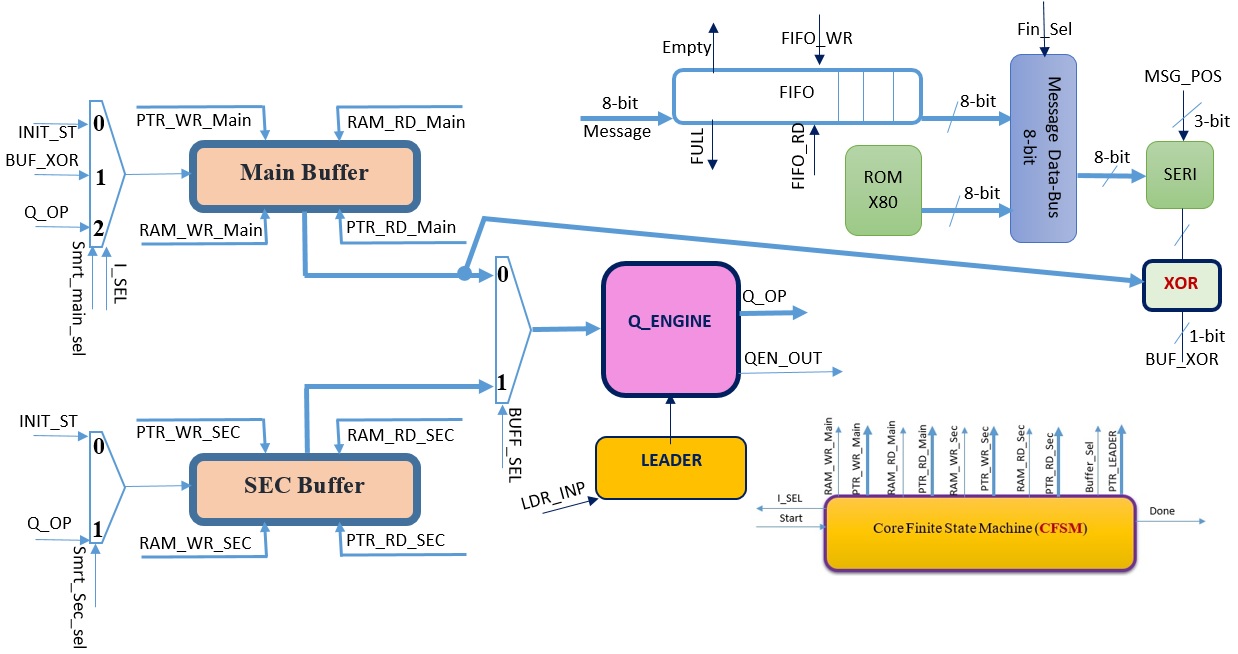
Attached is a block diagram describing one of the LWC candidates (GAGE processor using Buffers for generating the internal states of the algorithm with costing a few resources with around 164 microwatts using 28/32 nm technology (This processor called MICRO-GAGE). This processor has been designed and implemented by our team. The great part of this processor is the following: if you use a Ni-Cd battery (1200 mAh capacity at 1.2 V) and the processor runs at 909 MHz, the processor will continuously perform around 366 days without going idle for any instance of time while other candidates (Subterranean 2.0 will perform only for 138 days without going idle for any instance of time running at 100 MHz and consuming 432.4 microwatts.
The current project aims to extend the proposed co-processor to cover all the ten finalists of the LWC competition by attaching it with a RISC-V processor as a future cryptographic low-power solution, which also can be used for introducing low-latency internet of things postquantum cryptographic solution depending on the stateful hash-based signatures (LMS- produced by Cisco and XMSS, which is produced by NSA). To improve the reusability of the implementation, the algorithmically-complex part of the MICRO-GAGE processor will be implemented in the Chisel hardware construction language, which is a popular language choice for descriving tightly-coupled RISC-V accelerators.
3. Expected sustainability results, projected resource savings
This project will be covering the following performance metrics:
1) Throughput
2) Latency vs. the size of hashed/encrypted messages
3) Total consumed power
4) Estimation approach checks the ability of a different number of famous IoT graded batteries to process vast amounts of data by the introduced processor. For more info, please visit our current paper link: https://ieeexplore.ieee.org/document/9294948 and our space graded paper: https://ieeexplore.ieee.org/abstract/document/9546284
4. Design Introduction
Based on the statistics and public knowledge based on media and general reports posted by NASA, any space mission is costly in terms of time and funding for space missions. It is common knowledge that most space devices do not follow standard security protocols. Some might even wonder if there would be any attacks targeting these devices, to begin with. Unfortunately, there is a lot of interest from those who want to sabotage our space missions for multiple reasons, which have to be considered from the budget and design perspectives. For example, cube seats are usually tiny and run on solar cells fixed on the satellite's body. These cells provide constrained energy for doing the basic stuff for the mission; lightweight cryptography (LWC), in this case, is a great candidate to be ported into these devices as the number of computing resources and energy spent using these primitives is exceptionally tiny. Typically, both private and public space sectors will benefit from the current project in securing the tiny space devices. Space communication uses the traditional security primitives, which are costly in terms of both computing and energy perspectives. Our design is using LWC as a unique solution for securing tiny rovers, cube-satellites, or any space device that has any physical constrained to host the traditional heavy computing cryptographic primitives like AES, RSA, Hash functions (SHA-2, SHA-3, etc.)
Lightweight cryptography (LWC) is a new branch of security that adds security aspects to constrained physical devices such as actuators, tiny sensors, and others that work under the Internet of Things (IoT) umbrella. The purpose of the design is to mimic multiple tiny space rovers that need to communicate or do a mechanical action by moving around a particular obstacle through a secure channel. The channel's security depends on using multiple LWC primitives, which use both encryption and decryption schemes of these primitives for adding the security aspect to the system.
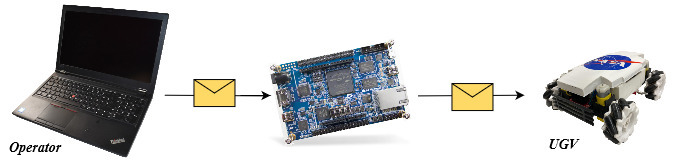
This project uses the DE10-Nano FPGA kit, which consists of both hardened 800MHz Dual-core ARM Cortex-A9 processors with 1 GB DDR3 SDRAM, which runs both real-time operating systems as RTOS or static operating systems as Linux and Cyclone V reconfigurable Fabric. In this project as a team, we are using the ARM processor for hosting a multiple LWC finalist that can be used to secure the data between multiple UGV. The DE10-Nano is used as a central security Hub between the UGVs for providing a secure channel between them. The whole system we are proposing is meant to be used for prototyping a scenario of a collaborative rover environment for space applications. We are aware of the limitation of DE10-Nano on the space computing side as it is not a rad-hard platform, but the extension of the work in space-graded platforms is our target. The current project is using the SoC on DE10-Nano to present the importance of SoC to host the LWC primitives, while in the future these primitives will be moved to the reconfigurable fabric on the board using both HDL languages and Quartus for creating one reconfigurable IP consisting of all of these LWC in both encryption and decryption modes. Fig 1, shows the detailed architecture of the proposed system.
Block Diagram:
Fig 1: Functional Diagram with DE-10 and IOT peripherals
5. Functional description and implementation
The project can be deconstructed into the following systems, which consist of the user-facing Operator module, the Security module, and the unmanned ground vehicle (UGV).
Figure 2: System Hierarchy
Operator
The operator system consists of user-facing software, which includes a Python-generated graphical user interface (GUI) from which mission waypoints can be selected. Using mission constraints and feedback regarding the terrain, a missions control team can select waypoints for desired paths and maneuvers. These waypoints are then captured and used to construct the payload. This payload is saved in JSON format and sent to the security module through a secure channel.
Figure 3: Interactive GUI to select waypoints
Security Module
The DE10-Nano Cyclone V SoC FPGA board functions as a secured information entry point for a field operational UGV. It receives encrypted information from the operator, decrypts it, and transmits the payload contents to the UGV. A python script receives input information and the desired lightweight cryptography scheme. Current cryptography schemes supported in our communication framework are Xoodyak, TinyJAMBU 128, TinyJAMBU 192, TinyJambu 256, and PHOTON-Beetle 128. The python script interfaces the information with a wrapper function for decryption, subsequently broadcasting this information to the designated target UGV’s.
Figure 4: Simulated UGV Mission in Virtual Environment
UGV
The process of designing an unmanned ground vehicle (UGV) that conforms to our stringent requirements of power, computational hardware, precision movement, and scalability necessitates the fabrication of a custom vehicle. Accordingly, the UGV was redesigned with modularity in mind, to allow for scalability and expansion.
Figure 5: CAD 3D Model of Rover
Figure 6: Model of UGV
As depicted above, the chassis accommodates four standard motors and gearboxes compatible with Mecanum wheels. The lightweight and scalable design allow for faster fabrication times, hot swapping in the case of an accident, and expansion slots for additional sensors.
Figure 7: Master-Slave UGV Control Circuit
Our designs utilize the entire frame space for Raspberry Pi’s, ESP32’s, battery holders, voltage regulators, and motor controllers. The schematic for the receiver can be seen in the above figure. Due to the ESP32’s dedicated PWM core, we use it for RTOS capabilities on the UGV.
6. Performance metrics, performance to expectation
Due to the typical environment it is used in, lightweight cryptography should be reasonably small such that it does not occupy too much storage in constrained devices. It should also be able to be executed in a reasonable amount of time in devices with low computing power. DE10-Nano is used to represent such devices. The resulting binary occupies 45 KB of space and the following are profiling statistics running different algorithms 1000 times each. As shown in Figure 8, the Xoodyak LWC primitive took around 130 msec for processing 4 byte messages with 4 bytes associated data. On the other hand, Figure 9, shows TinyJAMBU 128 takes 20 msec on processing the same message and associated data sizes. Furthermore, Figure 10, shows the results of TinyJAMBU 192 that takes 30 msec while Figure 11, shows the PHOTON-Beetle 128 cryptography took 5 seconds to encrypt the payload. All of these benchmarks were conducted on the same payload and under similar operating conditions to reduce the effects of external peripherals.
Figure 8: Xoodyak
Figure 9: TinyJAMBU 128
Figure 10: TinyJAMBU 192
Figure 11: PHOTON-Beetle 128
7. Sustainability results, resource savings achieved
There is a benefit in the area of the lightweight crypto that was translated. The first being that it is small. In the crypto being small this saves up a lot of space that could be utilized for other resources which allows for reuse of smaller older storage elements that may not be otherwise able to be utilized. The next one is that they take very little time to execute. This is self explanatory as the faster the execution the more encryption and decryption could occur, and therefore use less power for each execution. This is another area of ease to understand as the boon here is that the small power consumption leads to longer up times.
The IOT-centric design is based on scalability and reconfigurability in mind—it is made of modular elements that can be hot-swapped to both extend or manipulate our proposed communication network. The system design scheme consists of the DE10-Nano Cyclone V SoC FPGA board as a security hub, which provides encryption and decryption services for any number of UGVs in the system. In addition, the DE10-Nano is hosting multiple LWC finalist, which runs different variants of each LWC primitive for both security and battery limitations.
Fig 12: UGV Encryption Scheme
Fig 13: Software Flow Diagram
8. Conclusion
The current project continues our Reconfigurable Space Computing Laboratory activities at California State Polytechnic University, Pomona. In this project, we succeed in using the DE10-Nano as a central security Hub for hosting multiple LWC finalists while using this Hub to secure data between UGVs while performing different mechanical tasks. In the current status, one of the UGV has received the commands from the ground control station (Laptop), and these commands were encrypted and decrypted by DE10-Nano; once the UGV figured out the decrypted information, the wheels performed steady and stable movements around several obstacles (Memicing a scenario of rough terrain with a mission to pass this area with fewer damages). The current status of the project is the beginning of a long plan to use software/hardware partitioning approaches for getting better performance on the provided boards. The future design depends on having Avalon bus between the ARM processor and the created reconfigurable IP on the reconfigurable fabric with a thermal camera checking the heat activities on-chip for a better understanding of the effect of securing streaming massive data using DE10-Nano and the limitation of the board in terms of aging because of the heat distribution on-chip.
Acknowledgment
Special thanks to all the project members:
-
Antony Choi Yung
-
Dhanush Karthikeyan
-
Ruben Torres Romero
-
Shadrach Viste
Faculty Mentor:
-
Professor Mohamed El-Hadedy (Aly)
0 Comments
Please login to post a comment.